
Network Security
We are actively working on security protocols and methods for authentication as well as access control. To evaluate security properties, we also apply formal methods like model checking. We work with new protocols or modifications of existing protocols that use hardware security chips as the Trusted Platform Module (TPM) or Smart Cards.

Protection against DoS Attacks
Today (Distributed) Denial of Service Attacks are a major threat to the internet. In the past years there were attacks against the Internet infrastructure (i.e. DNS root servers), various services and companies and even against private persons using specific services (i.e. XBOX live). We are researching different ways to mitigate this threat.
Some networks are specially vulnerable against DoS attacks, for example if a core service that other services depend on has only limited capacity available. An attack against such a service will also affect dependend services. We are working on methods to check network and service topologies for such weaknesses.
Defense against ongoing attacks is easier if the defender has the possibility to flexibly re-configure his network topology. We are working on virtualization techniques that allow to change the network on the fly to limit the consequences on an attack.
Another research topic is the defense of HTTP-Servers by redirecting traffic between the client and multiple proxies. This way the attacker has to spend more resources to cause load on the server.
Honeypots, Malware Analysis and Intrusion Detection
In order to protect networks against Distributed Denial of Service Attacks understanding the mechanisms which are used to conduct these attacks is crucial.
Our research activities therefore deal with the investigation of malware and botnets. We employ different kinds of honeypots in order to collect worms and other kinds of malware. All collected malware is automatically analyzed in sandbox environments in order to gain knowledge about its functionality and the botnets which are build with it. Using the results of our analysis enables us to enhance our traffic analysis and intrusion detection methods.
Network Access Control and Applications of Trusted Computing Technology
We work on authentication and authorization in various areas of networking. Peer-to-Peer networks and other self-organising systems, Web Services, and sensor networks are some examples. Especially in the context of (partially) self-organising systems, we investigate solutions that go beyond classic X.509 PKI or shared key infrastructures.
To this end, we develop cryptographic protocols, especially for authentication and conduct security analyses. One way to do this is to apply methods of model checking. We also adapt yet unprotected applications and services to be able to use standardized state-of-the-art security solutions (TLS, IPSec, WS Security, XACML, …) with them.
We also work on security solutions that use the Trusted Platform Module (TPM) technology. One use-case for TPM is the secure storage of keys. Users cannot interfere and copy keys to insecure locations. The same is true for attackers who might want to get hold of the key to attack the network and its services. We also investigate Remote Attestation with the help of TPM. Remote Attestation allows to signal to another party that only a certain set of applications and a certain version of an Operating System (OS) is running on a computer. The primary usage is to avoid that worms, trojan horses or users of the system comprise its security by installing attack software. This is especially useful in business settings where even priviledged users could be attackers that need to be stopped.
Scientists: Michael Oberrauch, Dr. Holger Kinkelin, Dr. Johann Schlamp, Christian Dietze, Prof. Dr.-Ing. Georg Carle, Markus Sosnowski, M.Sc., Patrick Sattler, Stefan Genchev, M. Sc., Prof. Dr. Marc-Oliver Pahl, Lars Wüstrich, M. Sc., Lion Steger, Prof. Dr. Ralph Holz, Richard von Seck, Kilian Glas, Marcel Kempf, M.Sc., Tim Betzer, Filip Rezabek
Projects: ACE-SUPPRA, VITAF, AutoMon, DecADe, X-Check, SENDATE, securemail, SafeCloud, BaaS, SURF, IDEM, SpoVNet, Peeroskop, AutHoNe, ResumeNet, SASER, EINS, SecFuNet, ANSII
Publications (newest, Full list):
| 2024-03-01 | Filip Rezabek*, Marcin Bosk*, Leander Seidlitz, Jörg Ott, Georg Carle, “Context Matters: Lessons Learned from Emulated and Simulated TSN Environments,” in 3rd International Workshop on Negative Results in Pervasive Computing (PerFail 2024), Biarritz, France, Mar. 2024. [Pdf] [Bib] |
| 2024-01-01 | Burak Öz, Jonas Gebele, Parshant Singh, Filip Rezabek, Florian Matthes, “Playing the MEV Game on a First-Come-First-Served Blockchain,” Jan. 2024. [Preprint] [Bib] |
| 2023-11-01 | Burak Öz, Filip Rezabek, Jonas Gebele, Felix Hoops, Florian Matthes, “A Study of MEV Extraction Techniques on a First-Come-First-Served Blockchain,” Nov. 2023. [Preprint] [Bib] |
| 2023-06-01 | Marcin Bosk*, Filip Rezabek*, Johannes Abel, Kilian Holzinger, Max Helm, Georg Carle, Jörg Ott, “Simulation and Practice: A Hybrid Experimentation Platform for TSN,” in 22nd International Federation for Information Processing (IFIP) Networking Conference, Barcelona, Spain, Jun. 2023. [Bib] |
| 2023-03-01 | Filip Rezabek*, Marcin Bosk*, Georg Carle, Jörg Ott, “TSN Experiments Using COTS Hardware and Open-Source Solutions: Lessons Learned,” in 2nd International Workshop on Negative Results in Pervasive Computing (PerFail 2023), Atlanta, USA, Mar. 2023. Best Paper Award [Pdf] [Slides] [Bib] |

Blockchain Technology
Blockchains are one of the most interesting and relevant technologies that were created in recent years. Their initial purpose has been serving as a non-erasable and tamperproof ledger for decentralized payment systems. Besides this applicationo area, Blockchain technology can be used in other types of networked systems as a trusted building block comparable to a secure element in computer hardware.
For this reason, our first research focus are Trustworthy Networked Services based on Blockchain Technology. Furthremore, we perform Behavioral Analysis of Blockchains to better understand their network-related properties. Besides research, Blockchains play an important role in our courses.
Blockchain-Based Trustworthy Networked Services
The first focal point of our activities around Blockchains is our investigation how Blockchain technology can help us to build trustworthy and secure networked services. This includes research on federated identity management across different institutions, and secure and accountable configuration of networked devices.
Behavioral Analysis of Blockchains
Our chair has a long history in traffic measurement and analysis. For this reason, our second research focus on Blockchains is understanding their behavior in networks, and which effects Blockchains have on the network. Hence, we are currently building tools for our network test bed that allow us to conduct reproducible experiments with different Blockchain implementations in a controlled environment.
Courses
In our lecture on Peer-to-Peer Systems and Security (IN2194) there is currently a large chapter dedicated to this topic. Furthermore, we offer a Blockchain experiment in our lab course iLab2 (IN0012, IN2106, IN2257, IN4097, IN8018). Lastly, we offer topics on the subject in our seminars and pro seminar.
Further Information
You find further information about our activities on our B²TNS interest group page on this topic.
Scientists: Dr. Holger Kinkelin, Prof. Dr.-Ing. Georg Carle, Kilian Glas, Filip Rezabek
Projects: ACE-SUPPRA, VITAF, DecADe
Publications (newest, Full list):
| 2024-03-01 | Filip Rezabek*, Marcin Bosk*, Leander Seidlitz, Jörg Ott, Georg Carle, “Context Matters: Lessons Learned from Emulated and Simulated TSN Environments,” in 3rd International Workshop on Negative Results in Pervasive Computing (PerFail 2024), Biarritz, France, Mar. 2024. [Pdf] [Bib] |
| 2024-01-01 | Burak Öz, Jonas Gebele, Parshant Singh, Filip Rezabek, Florian Matthes, “Playing the MEV Game on a First-Come-First-Served Blockchain,” Jan. 2024. [Preprint] [Bib] |
| 2023-11-01 | Burak Öz, Filip Rezabek, Jonas Gebele, Felix Hoops, Florian Matthes, “A Study of MEV Extraction Techniques on a First-Come-First-Served Blockchain,” Nov. 2023. [Preprint] [Bib] |
| 2023-06-01 | Marcin Bosk*, Filip Rezabek*, Johannes Abel, Kilian Holzinger, Max Helm, Georg Carle, Jörg Ott, “Simulation and Practice: A Hybrid Experimentation Platform for TSN,” in 22nd International Federation for Information Processing (IFIP) Networking Conference, Barcelona, Spain, Jun. 2023. [Bib] |
| 2023-03-01 | Filip Rezabek*, Marcin Bosk*, Georg Carle, Jörg Ott, “TSN Experiments Using COTS Hardware and Open-Source Solutions: Lessons Learned,” in 2nd International Workshop on Negative Results in Pervasive Computing (PerFail 2023), Atlanta, USA, Mar. 2023. Best Paper Award [Pdf] [Slides] [Bib] |

Information Privacy
Privacy is another issue we are working on. This includes privacy in protocol design as well as anonymity on the Internet. Network security in general is related to many of our other research topics. Intrusion Detection is strongly related to monitoring. As Peer-to-Peer systems are increasingly used to improve classic client/server systems, securing Peer-to-Peer and other self-organising systems is in our focus.
Data privacy
Besides classical network security, the privacy has become an important topic of research. We focus on data protection and the control of data flows dudring full life-cycle in distributed systems. We therefore investigate which data emerges in cutting edge technology like smart buildings or smart cars and assess their criticality with respect to privacy. We then work on solutions how to better protect information, how to make data flows and their processing more transparent to the end user and we provide measures in order to let them stay in control of their own information.
Scientists: Dr. Holger Kinkelin, Prof. Dr.-Ing. Georg Carle, Lion Steger, Marcel Kempf, M.Sc., Filip Rezabek
Projects: ACE-SUPPRA, VITAF, DecADe, securemail, SafeCloud, IDEM, EINS
Publications (newest, Full list):
| 2024-03-01 | Filip Rezabek*, Marcin Bosk*, Leander Seidlitz, Jörg Ott, Georg Carle, “Context Matters: Lessons Learned from Emulated and Simulated TSN Environments,” in 3rd International Workshop on Negative Results in Pervasive Computing (PerFail 2024), Biarritz, France, Mar. 2024. [Pdf] [Bib] |
| 2024-01-01 | Burak Öz, Jonas Gebele, Parshant Singh, Filip Rezabek, Florian Matthes, “Playing the MEV Game on a First-Come-First-Served Blockchain,” Jan. 2024. [Preprint] [Bib] |
| 2023-11-01 | Burak Öz, Filip Rezabek, Jonas Gebele, Felix Hoops, Florian Matthes, “A Study of MEV Extraction Techniques on a First-Come-First-Served Blockchain,” Nov. 2023. [Preprint] [Bib] |
| 2023-06-01 | Marcin Bosk*, Filip Rezabek*, Johannes Abel, Kilian Holzinger, Max Helm, Georg Carle, Jörg Ott, “Simulation and Practice: A Hybrid Experimentation Platform for TSN,” in 22nd International Federation for Information Processing (IFIP) Networking Conference, Barcelona, Spain, Jun. 2023. [Bib] |
| 2023-03-01 | Filip Rezabek*, Marcin Bosk*, Georg Carle, Jörg Ott, “TSN Experiments Using COTS Hardware and Open-Source Solutions: Lessons Learned,” in 2nd International Workshop on Negative Results in Pervasive Computing (PerFail 2023), Atlanta, USA, Mar. 2023. Best Paper Award [Pdf] [Slides] [Bib] |

Traffic Measurement and Analysis
Overview
An important prerequisite for many network operation tasks today is the availability of traffic measurement functions that provide information about the current traffic characteristics with low latency. The resulting measurement data can then be analyzed and interpreted in order to classify the traffic into application classes, to detect malicious activities (e.g., worm outbreaks or botnet traffic), or to detect network malfunctions. Furthermore, communication patterns observed in a network allow inferring dependencies between different service, which is useful to identify the most critical components and end systems in a network.
Our research work focuses on the development and evaluation of novel passive traffic measurement functions, in particular for real-time packet-level and flow-level measurements, as well as the analysis of packet and flow data for traffic classification and the detection of attacks and anomalies. Furthermore, we contribute to standardization bodies, especially to the IETF.
Packet and Flow-based Traffic Measurement
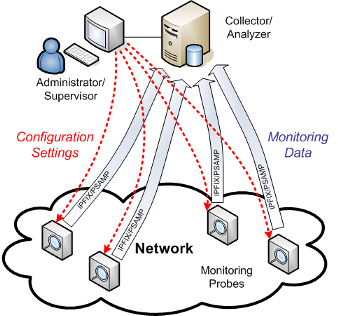
Packet-based traffic measurements deal with the capturing of traffic traces which contain packet header information and optionally parts of the payload as well. Typical systems performing packet-based traffic measurements are network analyzers and network-based intrusion detection systems which analyze the captured packets directly. However, it is also possible to capture the traffic at routers and network monitors which export the resulting measurement data to a remote analysis systems. A recent IETF standard for the export of packet reports to a remote collector is the PSAMP protocol specified in RFC5476.
Packet-based traffic measurements in high-speed networks require a lot of computational and memory resources. A less demanding alternative are flow-based traffic measurements which gather statistics about flows of packets sharing a set of common properties called flow keys. A typical set of flow keys consists of the IP quintuple of transport protocol, source IP address, destination IP address, source port, and destination port. The IETF standard for exporting flow records is the IPFIX protocol specified in RFC5101.
Our group is working on advanced monitoring and export functions for PSAMP and IPFIX compliant devices. For evaluation and practical deployment, we implement these advanced functions as software solutions, mainly in C and C++. Most of this implementation work takes place in the scope of the HISTORY project, which is a joint project with the University of Erlangen, aiming at the development of open-source software tools for high-speed network monitoring and analysis. The main software tool developed in this context is VERMONT, which is a modular monitoring probe supporting IPFIX and PSAMP export and collection.
Members of our group have been actively contributing to the standardization of IPFIX and PSAMP. In particular, we are working on a data model for configuring monitoring devices. Further standardization initiatives concern the secure and efficient transport of monitoring data using encryption and compression methods.
Attack and Anomaly Detection
The detection of harmful traffic caused by attacks, worms, or botnets still is an interesting research topic. Although abundant research work has been conducted in this area, the emergence of new security threats (e.g., flux and fast-flux botnets) and the ever changing characteristics of benign network utilization (e.g., mobile web 2.0 applications) require a continuous research effort.
One of our research activities in this area deals with the investigation of worm and botnet traffic. With the resulting knowledge, we develop innovative monitoring and detection functions which enable the detection of such malicious traffic with limited computational and memory resources. Furthermore, we work on methods for detecting traffic anomalies in flow data. Since many anomalies are the result of harmless traffic variations, the principal objective is to find appropriate traffic metrics and detection methods which are primarily sensitive to incidents which are of potential relevance for the network administrator.
Traffic Classification
Network operators are interested in identifying the traffic of different applications in order to monitor and control the utilization of the available network resources. Since the traffic of many new applications cannot be identified by specific port numbers, deep packet inspection (DPI) is the current technology of choice. However, DPI is very costly as it requires a lot of computational resources as well as up-to-date signatures of all relevant applications. Furthermore, DPI is limited to unencrypted traffic.
In order to overcome the limitations and drawbacks of port and content-based traffic classification, the development of statistical classification methods has become an important area of research. As part of the LUPUS project, our goal is to find new traffic properties and metrics which can be derived from passive traffic measurements and which allow us to better distinguish between different protocols and applications. Thereby, we concentrate on statistical methods which are easy to implement and to deploy in real networks.
Scientists: Michael Oberrauch, Johannes Späth, M.Sc., Max Helm, M. Sc., Dr. Johann Schlamp, Christian Dietze, Eric Hauser, Stefan Lachnit, M.Sc., Markus Sosnowski, M.Sc., Benedikt Jaeger, Manuel Simon, M.Sc., Patrick Sattler, Lion Steger, Prof. Dr. Ralph Holz, Marcel Kempf, M.Sc., Jonas Andre, M. Sc., Henning Stubbe, Tim Betzer, Kilian Holzinger
Projects: POST, SLICES-PP, 6G-life, 6G-ANNA, 6G Zukunftslabor Bayern – 6G Future Lab Bavaria, SLICES-SC, PRIMEnet, ModANet, AI4Performance, MOONSHINE, AutoMon, X-Check, SENDATE, I2RS, Vermont, Diadem Firewall, COST TMA, Peeroskop, DFG LUPUS, HISTORY - HIgh Speed neTwork mOnitoRing and analYsis, SASER
Publications (newest, Full list):
| 2024-12-01 | Johannes Späth, Max Helm, Benedikt Jaeger, Georg Carle, “Sim2HW: Modeling Latency Offset Between Network Simulations and Hardware Measurements,” in Proceedings of the 3rd GNNet Workshop: Graph Neural Networking Workshop (GNNet ’24), Los Angeles, CA, USA, Dec. 2024. [Pdf] [Homepage] [Rawdata] [DOI] [Bib] |
| 2024-10-01 | Alexander Daichendt, Florian Wiedner, Jonas Andre, Georg Carle, “Applicability of Hardware-Supported Containers in Low-Latency Networking,” 20th International Conference on Network and Service Management (CNSM 2024), Oct. 2024. [Pdf] [Homepage] [Bib] |
| 2024-10-01 | Manuel Simon, Sebastian Gallenmüller, Georg Carle, “On-the-fly Table Insertions on Programmable Software Data Planes,” in 20th International Conference on Network and Service Management (CNSM 2024), Prague, Czech Republic, Oct. 2024. [Preprint] [Slides] [Bib] |
| 2024-10-01 | Richard von Seck, Filip Rezabek, Georg Carle, “Thresh-Hold: Assessment of Threshold Cryptography in Leader-Based Consensus,” in 2024 IEEE 49th Conference on Local Computer Networks (LCN), Oct. 2024, pp. 1–8. [Bib] |
| 2024-09-01 | Henning Stubbe, Sebastian Gallenmüller, Manuel Simon, Eric Hauser, Dominik Scholz, Georg Carle, “Exploring data plane updates on P4 switches with P4Runtime,” Computer Communications, vol. 225, pp. 44–53, Sep. 2024. [Url] [Pdf] [DOI] [Bib] |

Software Defined Networking
Software-defined networking (SDN) allows the separation of networks into a lower-level data plane and a higher-level control plane. The former performs the actual packet forwarding task whereas the latter allows centralized control and management for computer networks. This concept - originally from academia - gained additional support by industry, where SDN enables the development of innovative and radically new applications for users like data centers or Internet providers.
We apply SDN in different areas of our activity. One area is the development of new concepts that combine security and monitoring with systematic performance analysis of Virtual Network Functions (VNF) and Network Function Chaining (NFC). This includes measuring and modeling of virtualization technologies in NFC setups using network functions such as Firewalls, Load Balancing, or Deep Packet Inspection (DPI). Another area of research is the development of solutions for secure and scalable communication network infrastructures achieving cost-efficient, energy-efficient, reliable, and stable routing. These developments include flow-based network monitoring and network security applications. The design and development of an observational analysis system for the network’s backbone routing is also part of ongoing research. Core components are mechanisms allowing information fusion and classification for understanding the impact of SDN on backbone networks. For research purpose, the chair maintains its own testbed featuring SDN-enabled hardware and software as well as a toolset for high-speed traffic measurements. Utilizing this testbed allows us to investigate the feasibility of multicore systems for high-speed packet processing. Moreover, methods for performance evaluation and improvement of packet processing were developed, to gain an understanding of the interaction between various hardware and software components.

Formal Methods for SDN Security Administration (FM-SDN-SA)
One area of our SDN-related research is to apply formal methods for security administration of Software-Defined Networks. This work has been performed in part in connection the EU project EINS, the Network of Excellence on Internet Science. A huge part of a network's security depends on its configuration and administration. Network segmentation and isolation prevent unauthorized accesses and information leakage. It is a well-known fact in the area of firewalls that configuring and administrating network security policies is an error-prone process.
Our work focuses on two aspects: First, we provide tool support to understand existing, legacy network configurations and migrate them to SDN. Second, we develop methods to ease the inherent management complexity. Both aspects focus on tool support and automation to prevent human error. It is important not to replace human error with errors in our tools; consequently, all our methods are machine-verifiable proven correct with the Isabelle/HOL theorem prover. Aspect one: It is important to understand existing, legacy network configuration before a network can be migrated to SDN. We focus one specific technology: Linux/netfilter iptables. The iptables firewall is wide-spread, real-world approved, and supports many features. Consequently, there are numerous configurations which utilize a vast amount of features, and as many deployments exist for a long time, many configurations are no longer fully understood by their administrator(s). We have collected many such configurations and developed scientific methods to understand challenging configurations. These methods have a large potential to be applied to other SDN-related network technologies. We provide a formal semantics for iptables packet filtering. Given those formal foundations, we provide tools to check BCP 38 and visualize the network access control policies implied by a firewall. Current work includes translating iptables and routing configuration to the Open vSwitch in a fully automated and fully machine-verified manner. Aspect two: Managing access control policies by hand scales quadratically with the number of (logical) network participants. Consequently, managing access control policies by hand is error prone. We have shown that even advanced administrators may make errors for policies with only ten hosts. To conquer this complexity challenge, we provide management methods on higher abstraction layers. We have presented a full toolchain to automatically translate network security invariants to Open vSwitch and iptables configurations. Those high-level security invariants directly encode the scenario-specific security requirements, are modular and composable, and can be securely auto-completed. Consequently, managing security invariants instead of low-level access control policies removes inherent complexity and can thus prevent human error. In addition, our tool can give feedback about the specified invariants and verify existing configurations – e.g. obtained by (aspect one) – against such invariants.
Scientists: Max Helm, M. Sc., Eric Hauser, Stefan Lachnit, M.Sc., Prof. Dr.-Ing. Georg Carle, Benedikt Jaeger, Manuel Simon, M.Sc., Sebastian Gallenmüller, Jonas Andre, M. Sc., Henning Stubbe, Kilian Holzinger
Projects: HYPERNIC, AI4Performance, SENDATE, I2RS, SASER, EINS, SecFuNet
Publications (newest, Full list):
| 2024-12-01 | Johannes Späth, Max Helm, Benedikt Jaeger, Georg Carle, “Sim2HW: Modeling Latency Offset Between Network Simulations and Hardware Measurements,” in Proceedings of the 3rd GNNet Workshop: Graph Neural Networking Workshop (GNNet ’24), Los Angeles, CA, USA, Dec. 2024. [Pdf] [Homepage] [Rawdata] [DOI] [Bib] |
| 2024-10-01 | Manuel Simon, Sebastian Gallenmüller, Georg Carle, “On-the-fly Table Insertions on Programmable Software Data Planes,” in 20th International Conference on Network and Service Management (CNSM 2024), Prague, Czech Republic, Oct. 2024. [Preprint] [Slides] [Bib] |
| 2024-09-01 | Henning Stubbe, Sebastian Gallenmüller, Manuel Simon, Eric Hauser, Dominik Scholz, Georg Carle, “Exploring data plane updates on P4 switches with P4Runtime,” Computer Communications, vol. 225, pp. 44–53, Sep. 2024. [Url] [Pdf] [DOI] [Bib] |
| 2024-08-01 | Manuel Simon, Henning Stubbe, Sebastian Gallenmüller, Georg Carle, “Honey for the Ice Bear - Dynamic eBPF in P4,” in Proceedings of the ACM SIGCOMM 2024 Workshop on EBPF and Kernel Extensions, New York, NY, USA, Aug. 2024, pp. 44–50. [Url] [Pdf] [Preprint] [Slides] [Sourcecode] [DOI] [Bib] |
| 2024-05-01 | Lars Wüstrich, Sebastian Gallenmüller, Stephan Günther, Georg Carle, Marc-Oliver Pahl, “Shells Bells: Cyber-Physical Anomaly Detection in Data Centers,” in 2024 IEEE/IFIP Network Operations and Management Symposium (NOMS 2024), Seoul, Korea, May 2024. [Pdf] [Bib] |

QUIC
Research of the new QUIC protocol has been a priority at our chair since the early stages of the IETF draft. Our research focuses on the performance of QUIC on high-speed networks but also the protocol deployment on the Internet.
Performance Measurements
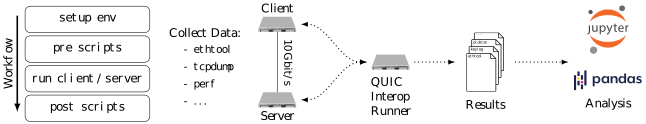
We conduct performance measurements of the QUIC protocol and different implementations on testbeds of our chair. All measurements are conducted on real hardware and focus on high-speed scenarios with links of 10Gbit/s or higher. We evaluate different libraries such as LSQUIC, Quiche and quic-go. Measurements are conducted in different scenarios and under different network conditions. Therefore, we developed a framework to enable high-speed network measurements on dedicated hardware servers. It is based on the QUIC Interop Runner and follows different principles: flexibility, portability and reproducibility.
Deployment Identification
Besides performance measurements, we analyze QUIC deployments on the Internet based on large-scale scans. We developed tools to scan QUIC and identify libraries used by the server. We conduct weekly scans and evaluate the state of QUIC deployments and their development over time.
Scientists: Johannes Späth, M.Sc., Benedikt Jaeger, Lion Steger, Marcel Kempf, M.Sc.
Projects: PRIMEnet
Publications (newest, Full list):
| 2024-06-01 | Marcel Kempf, Nikolas Gauder, Benedikt Jaeger, Johannes Zirngibl, Georg Carle, “A Quantum of QUIC: Dissecting Cryptography with Post-Quantum Insights,” in International Federation for Information Processing (IFIP) Networking Conference 2024, Thessaloniki, Greece, Jun. 2024. [Preprint] [Rawdata] [DOI] [Bib] |
| 2024-05-01 | Markus Sosnowski, Patrick Sattler, Johannes Zirngibl, Tim Betzer, Georg Carle, “Propagating Threat Scores With a TLS Ecosystem Graph Model Derived by Active Measurements,” in Proc. Network Traffic Measurement and Analysis Conference (TMA), May 2024. [Pdf] [Slides] [Homepage] [DOI] [Bib] |
| 2024-03-01 | Johannes Zirngibl, Florian Gebauer, Patrick Sattler, Markus Sosnowski, Georg Carle, “QUIC Hunter: Finding QUIC Deployments and Identifying Server Libraries Across the Internet,” in Passive and Active Measurement Conference (PAM), Mar. 2024. [Homepage] [DOI] [Bib] |
| 2023-12-01 | Patrick Sattler, Johannes Zirngibl, Mattijs Jonker, Oliver Gasser, Georg Carle, Ralph Holz, “Packed to the Brim: Investigating the Impact of Highly Responsive Prefixes on Internet-wide Measurement Campaigns,” Proc. ACM Netw., vol. 1, no. CoNEXT3, Dec. 2023. [Url] [Pdf] [Homepage] [DOI] [Bib] |
| 2023-07-01 | Johannes Naab, Patrick Sattler, Johannes Zirngibl, Stephan Günther, Georg Carle, “Gotta Query ’Em All, Again! Repeatable Name Resolution with Full Dependency Provenance,” in Proceedings of the Applied Networking Research Workshop, Jul. 2023. [Pdf] [Rawdata] [Bib] |

Future Internet
The Internet was designed about 40 years ago, and initially was intended as a means of communication only for a relatively small group of people in academic and research contexts. As we all know, the Internet has meanwhile experienced an enormous growth; the number of hosts and thus the number of users has grown by several orders of magnitude. At the same time, some assumptions that drove the Internet's original design are no longer true today: An increasing number of end devices is mobile and thus frequently changes its location in the topology. Not only some users, but end hosts and even entire networks
Scientists: Stefan Genchev, M. Sc., Prof. Dr. Marc-Oliver Pahl, Lars Wüstrich, M. Sc., Henning Stubbe
Projects: SafeCloud, BaaS, AutHoNe, ResumeNet, EINS, SecFuNet, OpenLab-Eclectic
Publications (newest, Full list):
| 2018-02-01 | F. Helfert, H. Niedermayer, G. Carle, “Evaluation of Algorithms for Multipath Route Selection over the Internet ,” in 14th International Workshop on Design of Reliable Communication Networks (DRCN), Feb. 2018. [Pdf] [Bib] |
| 2016-09-01 | Daniel Sel, Sree Harsha Totakura, Georg Carle, “sKnock: Scalable Port-Knocking for Masses ,” in Workshop on Mobility and Cloud Security & Privacy, Budapest, Hungary, Sep. 2016. [Preprint] [Sourcecode] [Bib] |
| 2016-05-01 | Cornelius Diekmann, Julius Michaelis, Maximilian Haslbeck, Georg Carle, “Verified iptables Firewall Analysis,” in IFIP Networking 2016, Vienna, Austria, May 2016. [Url] [Pdf] [Slides] [Sourcecode] [Rawdata] [Bib] |
| 2015-11-01 | Cornelius Diekmann, Lukas Schwaighofer, Georg Carle, “Certifying Spoofing-Protection of Firewalls,” in 11th International Conference on Network and Service Management, CNSM, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Sourcecode] [Rawdata] [DOI] [Bib] |
| 2015-11-01 | Cornelius Diekmann, Andreas Korsten, Georg Carle, “Demonstrating topoS: Theorem-Prover-Based Synthesis of Secure Network Configurations,” in 2nd International Workshop on Management of SDN and NFV Systems, manSDN/NFV, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Slides] [Sourcecode] [DOI] [Bib] |

Peer-to-Peer and Overlay Networks
Overview
Overlay networks change the structure of a network to a structure of their need. Applications organize and manage their networks. Peer-to-Peer overlays allow to utilize resources at the edges of the network – resources from service providers as well as home users. The decentralized nature of the Peer-to-Peer paradigm allows new ideas, but also leads to additional problems with respect to security and service quality. We research on improving resilience with Peer-to-Peer methods, on security for overlay networks in general, spontaneous networks, and on the optimization of overlay networks using Cross-Layer information and measurements.
Resilience of P2P Systems
Peer-to-Peer networks provide a diversity of nodes and links that is unknown to the classic Client/Server Internet. This is beneficial for all services that profit from diversity. In the project ResumeNet we work on improving the resilience of networked service in future networks. The use of Peer-to-Peer methods is our first choice.
We adapted and studied the use of the Kademlia/KAD DHT to lookup services. Even when a lot of nodes fail a lookup can succeed. Future DNS service could also be more resilient with this kind of service resilience. Network resilience is based on the idea to use different additional route to the traditional IP routing. In case of failures or triangular inequality violations one may use overlay routes to improve performance or resolve failures.
Security and Privacy
Authentication and Authorization in Peer-to-Peer systems is usually delegated to a server. We developped new means to overcome this limitation and still provide reasonable security. The idea is to use social structures of humans behind the peers to form clusters of nodes that operate as one clique (or domain). The more scalable level of the cliques is used to build trust between the "servers" of different cliques. As trust establishment needs to deal with yet untrusted potentially insecure cases, we propose to include a risk assessment in the authentication and authorization process. Applications can then decide if they interact in order to build trust or skip the communication.
We also study attacks and defenses against Peer-to-Peer systems, in particular the Sybil and Eclipse attack. The increasing combination of social networks and Peer-to-Peer systems is not only used for security, but also studied in order to preserve the privacy of users.
Spontaneous Networks
Spontaneous Networks are formed spontaneously to provide a certain functionality for some time. Together with other partners we developped an architecture for such networks in the SpoVNet project. We expect that future services will utilize service-specific networks in a Future Internet. Given enough diversity, spontaneous interactions of hetergeneous systems will be a building-block in future networks.
Cross-Layer Measurement and Optimization
CLIO and UNISONO are our tools to collect and measure Cross-Layer information. UNISONO is a generic tool that operates within the system. CLIO adapts spontaneous overlays from the SpoVNet project to UNISONO. In SpoVNet, we use this to optimize multicast and video services.
Combining Server and P2P Infrastructures
The P2P paradigm has advantages and disadvantages. The Client/Server paradigm also has advantages and disadvantages. The idea here is that we could benefit from the advantages of both if we combine server and P2P system properly. The project CoSIP improve resilience for VoIP signalling using a server for performance and a P2P network for resilience when the server is unreachable. In other work we study the interaction of Cloud Computing and Peer-to-Peer. This may allow normal home users to benefit from the advent of Cloud Computing and lead to new kinds of applications.
Scientists: Prof. Dr. Ralph Holz, Richard von Seck
Projects: SpoVNet, Multimedia Conferencing, ResumeNet, OpenLab-Eclectic
Publications (newest, Full list):
| 2009-11-01 | Dirk Haage, Ralph Holz, “Optimization of Distributed Services with UNISONO (ext. abstract),” in GI/ITG KuVS Fachgespräch NGN Service Delivery Platforms & Service Overlay Networks, Berlin, Germany, Nov. 2009. [Bib] |
| 2009-11-01 | Ralph Holz, Dirk Haage, “CLIO/UNISONO: Practical Distributed and Overlay-Wide Network Measurement (ext. abstract),” in 4th GI/ITG KuVS Workshop on The Future Internet and 2nd Workshop on Economic Traffic Management (ETM), Zürich, Switzerland, Nov. 2009. [Bib] |
| 2009-03-01 | Dirk Haage, Ralph Holz, Heiko Niedermayer, Pavel Laskov, “CLIO – A Cross-Layer Information Service for Overlay Network Optimization,” in Kommunikation in Verteilten Systemen (KiVS) 2009, Kassel, Germany, Mar. 2009. [Pdf] [Homepage] [Bib] |
| 2007-07-01 | Oliver Waldhorst, Roland Bless, Dirk Haage, et. al., “SpoVNet: An Architecture for Supporting Future Internet Applications,” in 7th Würzburg Workshop on IP: Joint EuroFGI and ITG Workshop on "Visions of Future Generation Networks", Würzburg, Germany, Jul. 2007. [Bib] |

Autonomic Networks / Self-Management
Networks have become ubiquitous in our lives. The humanity is dependent on a functioning of a multitude of different networks. Even for experts, manually running these networks has grown to a increasingly difficult task close to impossibility. It is therefore indispenable to increase management automation up to a state of autonomy.
Not only larger operator controlled networks are important also smaller scale networks have a growing importance. More and more devices in our houses and our everyday lives have networking capabilities to offer advanced functionality.
We target management automation from several directions.
Content-Centric Management for Future Networks
We are currently developing a platform for secure distributed autonomic content-centric management. Our aim is to contribute to the standardization of a network management that meets the requirements of today.
With the raising amount of technical equipment in our daily environments (e.g. at home), autonomic functionality becomes necessary to automatically integrate new hardware. With the abstraction of our platform new applications become possible that make life more agreeable…
Besides the core architecture our special research interests are Remote Access, Trust mechanisms, Security as well as Services and Applications for networks with our new autonomic mechanisms.
Large Multitechnology Operator controlled networks
Management of Operator Networks, especially mobile networks has grown very complicated for several reasons.
There is a increasing number of access technologies that are used within a single network. Several generations of the same technologies have to be seamlessly integrated to provide a unique user experience. As for example the parallel operation of 2G, 3G and 3.5G networks. In the future additional radio technologies as for example LTE or WiMAX will be integrated in the same way. Operators have to handle the large number of Network Elements but also have to provide a fine tuned configuration to enable seamless operation between different access networks. In order to handle those heterogeneous multi vendor networks with their complex inderdependencies new management concepts are required. We focus to provide a system that offers a high degree of automation and aims at autonomic management while stilll beeing under full operator control. Operation and maintenance staff should be freed from time consuming standard tasks to allow them to focus on critical situations and the optimization of the network. In case the automated functions do not act as expected the operator still has the possibliity to overrule the system.
Such an autonomic management system requires a way to include operational experience and the possibility to dynamically adapt to the current context.
Scientists: Johannes Späth, M.Sc., Dr. Holger Kinkelin, Prof. Dr.-Ing. Georg Carle, Prof. Dr. Marc-Oliver Pahl
Projects: AutHoNe
Publications (newest, Full list):
| 2012-10-01 | Thomas Kothmayr, Corinna Schmitt, Wen Hu, Michael Bruenig, Georg Carle, “A DTLS Based End-To-End Security Architecture for the Internet of Things with Two-Way Authentication,” in Seventh IEEE International Workshop on Practical Issues in Building Sensor Network Applications (SenseApp), Clearwater (FL), USA, Oct. 2012. [Bib] |
| 2011-11-01 | Thomas Kothmayr, Wen Hu, Corinna Schmitt, Michael Brünig, Georg Carle, “Securing the Internet of Things with DTLS,” in Proceedings of the 9th ACM Conference on Embedded Networked Sensor Systems (SenSys), Poster Session, Seattle, USA, Nov. 2011. [Bib] |
| 2011-09-01 | Lothar Braun, Corinna Schmitt, Benoit Claise, Georg Carle, “Compressed IPFIX for smart meters in constrained networks.” Internet-Draft (work in progress), draft-braun-core-compressed-ipfix-03.txt, Sep-2011. [Url] [Bib] |
| 2010-09-01 | Alexander Klein, Lothar Braun, Corinna Schmitt, Georg Carle, “MAUS: A Multi-hop Autonomous Sensor Network for Monitoring Applications with Full IP-support,” in Proceedings of the 9. GI/ITG KuVS Fachgespräch Sensornetze (FGSN), Würzburg, Germany, Sep. 2010. [Bib] |
| 2010-08-01 | Holger Kinkelin, Andreas Müller, Georg Carle, “Security and Access control for future home networks.” Demo at IPTComm 2010, Munich, Germany, Aug-2010. [Bib] |

Wireless Networks
Wireless networks have become ubiquitous. Ranging from large scale public switched telephone networks downto Wireless Sensor networks they have become part of our daily life. The large number of different interconnected networks, network technologies and devices leads to an unpreceded level of heterogeneity and complexity with strong impacts on management and operation. For us, topics of special interest are autonomic configuration, efficient operation and a high level of security.
Scientists: Prof. Dr.-Ing. Stephan M. Günther, Jonas Andre, M. Sc.
Projects: MOONSHINE, Wireless Sensor Network Research, ScaleNet SYMPATHIE
Publications (newest, Full list):
| 2023-01-01 | Marco Hoffmann, Gerald Kunzmann, Torsten Dudda, Ralf Irmer, Admela Jukan, Gordana Macher, Abdullah Ahmad, Florian R. Beenen, Arne Bröring, Felix Fellhauer, Gerhard Fettweis, Frank H. P. Fitzek, Norman Franchi, Florian Gast, Bernd Haberland, Sandra Hoppe, Sadaf Joodaki, Nandish P. Kuruvatti, Chu Li, Miguel Lopez, Fidan Mehmeti, Thomas Meyerhoff, Lorenzo Miretti, Giang T. Nguyen, Mohammad Parvini, Rastin Pries, Rafael F. Schaefer, Peter Schneider, Dominic Schupke, Stephanie Strassner, Henning Stubbe, Andra M. Voicu, “A secure and resilient 6G architecture vision of the German flagship project 6G-ANNA,” IEEE Access, 2023. [Pdf] [DOI] [Bib] |
| 2020-01-01 | Samuele Zoppi, Onur Ayan, Fabio Molinari, Zenit Music, Sebastian Gallenmüller, Georg Carle, Wolfgang Kellerer, “NCSbench: Reproducible Benchmarking Platform for Networked Control Systems,” in 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC) (CCNC 2020), Las Vegas, USA, Jan. 2020. [Pdf] [Bib] |
| 2019-03-01 | Sebastian Gallenmüller, René Glebke, Stephan Günther, Eric Hauser, Maurice Leclaire, Stefan Reif, Jan Rüth, Andreas Schmidt, Georg Carle, Thorsten Herfet, Wolfgang Schröder-Preikschat, Klaus Wehrle, “Enabling Wireless Network Support for Gain Scheduled Control,” in 2nd International Workshop on Edge Systems, Analytics and Networking (EdgeSys ’19), Dresden, Germany, Mar. 2019. [Url] [Pdf] [DOI] [Bib] |
| 2019-01-01 | Zenit Music, Fabio Molinari, Sebastian Gallenmüller, Onur Ayan, Samuele Zoppi, Wolfgang Kellerer, Georg Carle, Thomas Seel, Jörg Raisch, “Design of a Networked Controller for a Two-Wheeled Inverted Pendulum Robot,” IFAC-PapersOnLine, vol. 52, no. 20, pp. 169–174, 2019. [Pdf] [Bib] |
| 2018-04-01 | Sebastian Gallenmüller, Stephan Günther, Maurice Leclaire, Samuele Zoppi, Fabio Molinari, Richard Schöffauer, Wolfgang Kellerer, Georg Carle, “Benchmarking Networked Control Systems,” in 1st Workshop on Benchmarking Cyber-Physical Networks and Systems, Oporto, Portugal, Apr. 2018. [Pdf] [Bib] |

Resilience
By taking part in the EU FP 7 project RESUMENET (Resilience and Survivability for future networking - framework, mechanisms and experimental evaluation) our research focus shifted towards more resilience-oriented research questions. An example were applications that were uninterupted by changes in location and server due to mobility or failure. Another idea was to use Peer-to-Peer solutions in combination with client-server solutions (CoSIP) using the peers as fall-back. In the EINS network of excellence, we explored the implications of Internet as Critical Infrastructure, on a technical side, but also addressing the multi-disciplinary aspects of the research problem (e.g. with management sciences and social sciences). Finally, there is some work on network planning and modelling. Here we use optimization methods and network calculus.
Scientists: Dr. Johann Schlamp, Kilian Holzinger
Projects: RECODIS, SafeCloud, ResumeNet, EINS
Publications (newest, Full list):
| 2019-05-01 | Cora Perner, Georg Carle, “Comparison of Optimization Goals for Resilient Routing,” in 2019 IEEE International Conference on Communications Workshops (ICC Workshops): The 2nd International Workshop on 5G and Cooperative Autonomous Driving (5G Auto) (ICC 2019 Workshop - 5G Auto), Shanghai, P.R. China, May 2019. [Bib] |
| 2018-02-01 | F. Helfert, H. Niedermayer, G. Carle, “Evaluation of Algorithms for Multipath Route Selection over the Internet ,” in 14th International Workshop on Design of Reliable Communication Networks (DRCN), Feb. 2018. [Pdf] [Bib] |
| 2016-05-01 | Cornelius Diekmann, Julius Michaelis, Maximilian Haslbeck, Georg Carle, “Verified iptables Firewall Analysis,” in IFIP Networking 2016, Vienna, Austria, May 2016. [Url] [Pdf] [Slides] [Sourcecode] [Rawdata] [Bib] |
| 2015-11-01 | Cornelius Diekmann, Lukas Schwaighofer, Georg Carle, “Certifying Spoofing-Protection of Firewalls,” in 11th International Conference on Network and Service Management, CNSM, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Sourcecode] [Rawdata] [DOI] [Bib] |
| 2015-11-01 | Cornelius Diekmann, Andreas Korsten, Georg Carle, “Demonstrating topoS: Theorem-Prover-Based Synthesis of Secure Network Configurations,” in 2nd International Workshop on Management of SDN and NFV Systems, manSDN/NFV, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Slides] [Sourcecode] [DOI] [Bib] |

ixy: Safe and Secure Network Drivers
Drivers are usually written in C for historical reasons, this can be a problem for safety and security. We are working on drivers called ixy (diminutive form of ixgbe) for 10 Gbit/s network cards written in high-level programming languages ranging from Rust to Haskell. The main goal is to show trade-offs when writing drivers in safer languages than C: How do language safety features affect performance? Are all languages suitable for drivers?
Eductional Drivers
A second goal is to use ixy for educational purposes. Drivers are often seen as untouchable black-boxes by developers and researchers because they seem hard to write and understand. Our drivers are all in the order of 1000 lines of code with documentation, comments, and pointers to further reading material such as specific sections in data sheets.
Performance
Safety features of languages often cost performance, we try to quantify and model the impacts of specific safety features using both white-box and black-box benchmarking methods. Results show that some languages like Rust can achieve almost the same performance as C code while preventing memory errors.
Further Information
Ongoing work is summarized in a project on GitHub with links to all implementations.
Scientists:
Projects:

